Peace be upon you. Here I will walk through how I solved this challenge and achieved First Blood.
The challenge provided a ZIP archive containing the following files:
As a lazy geek, my usual approach to forensics challenges is to work smart, not hard. My first step was to focus on file modification timestamps. I listed all challenge files by their last modification date using the following Linux command:
find . -type f -printf '%T@ %p\n' | sort -nr | cut -d' ' -f2- > mod.txt
I opened the ActivitiesCache.db file, which stores all user activities on Windows. Using DB Browser for SQL, I navigated through it to get a high-level view of the user’s activity.
.png)
I also used WxTCMD from Eric Zimmerman’s tools, which can parse and translate the activity type column values:
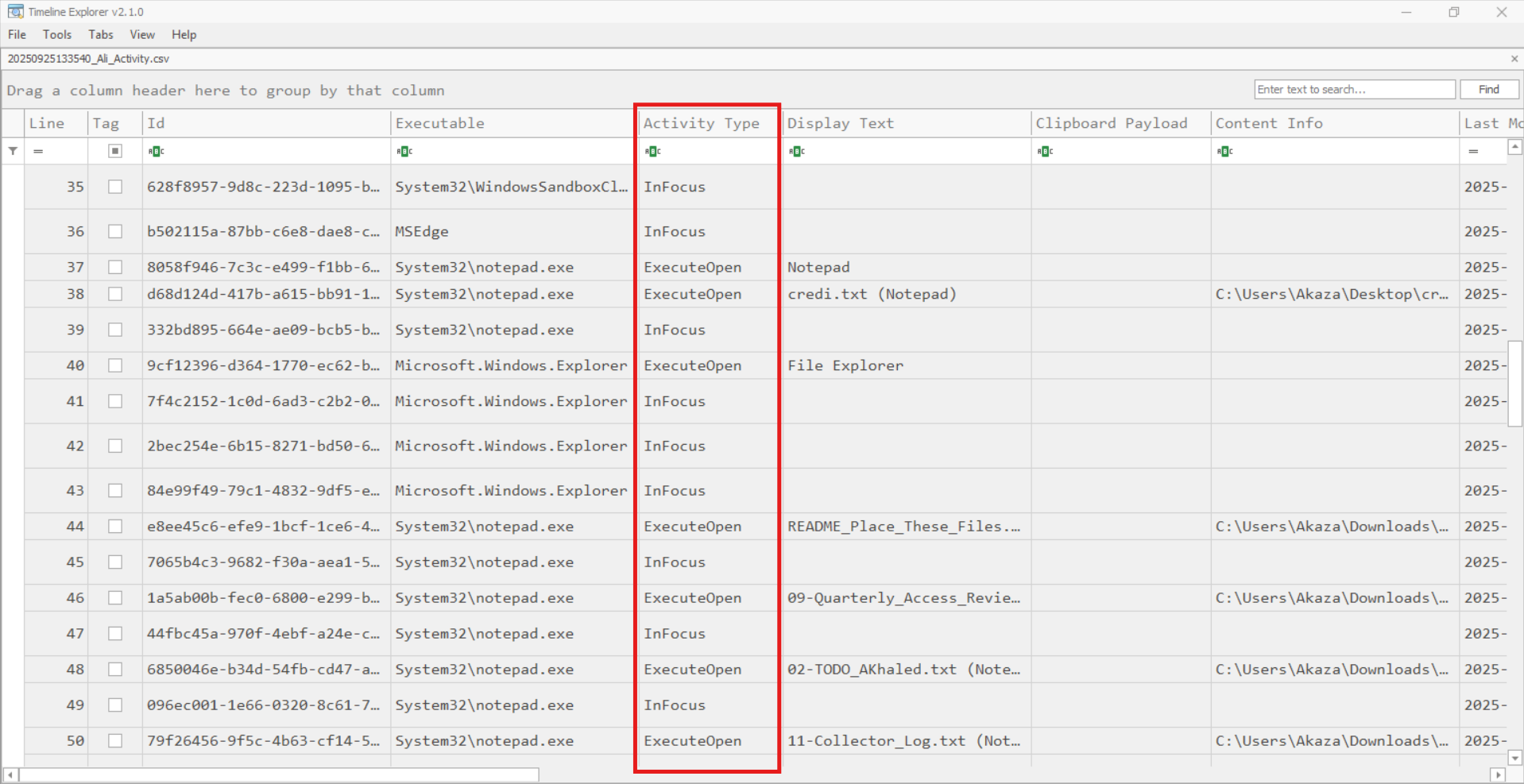
From this, I discovered that the user had been using Notepad to view several text files, including credi.txt on the Desktop and others located under the Notepad_content_ folder in Downloads.
To view the contents of these files, I searched through the challenge files for the path C:\Users\Akaza\Downloads\. However, I only found the AppData folder and NTUSER files under the Akaza user directory.
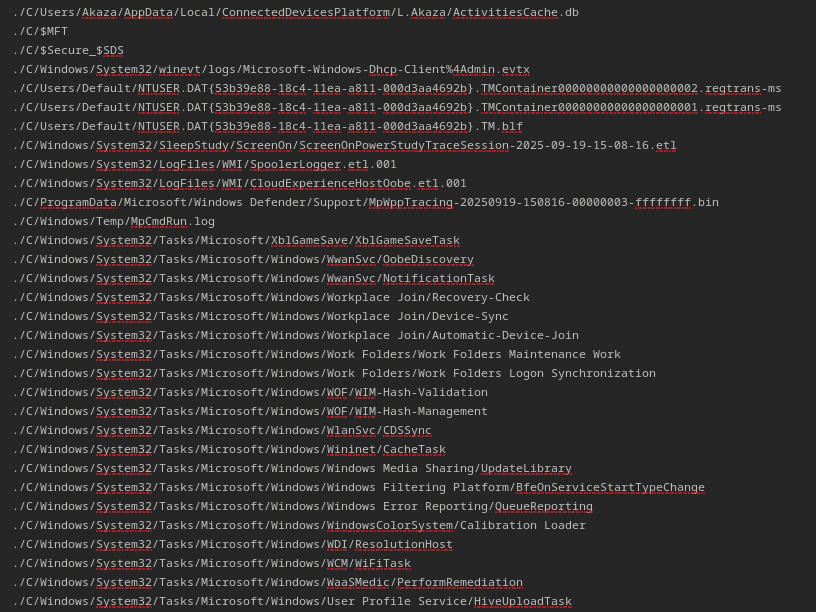
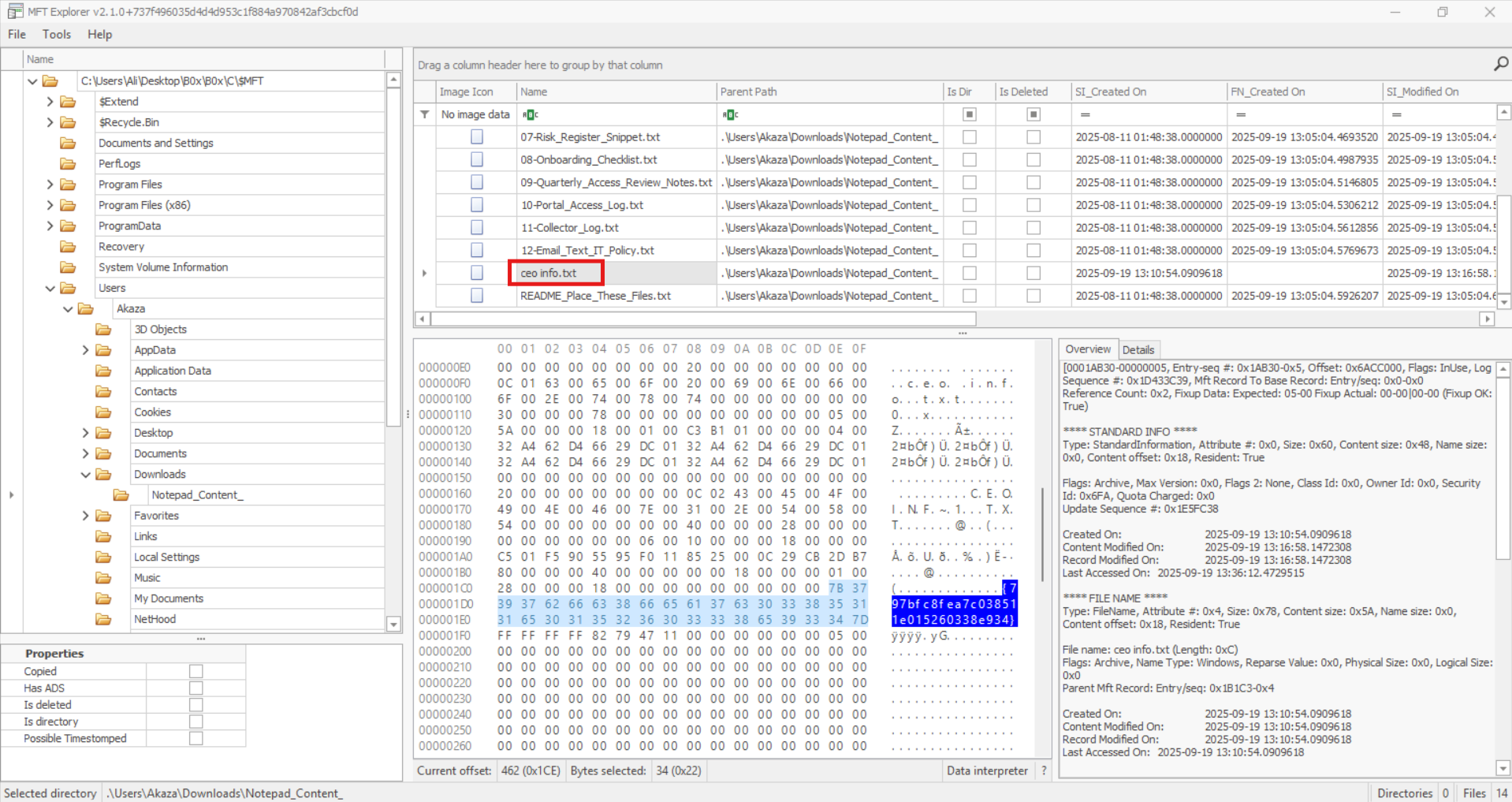
Next, I examined the second most recently modified file: MFT. I opened it with MFT Explorer, which revealed all the paths I needed. Using the hex viewer, I could inspect the contents of the relevant files:
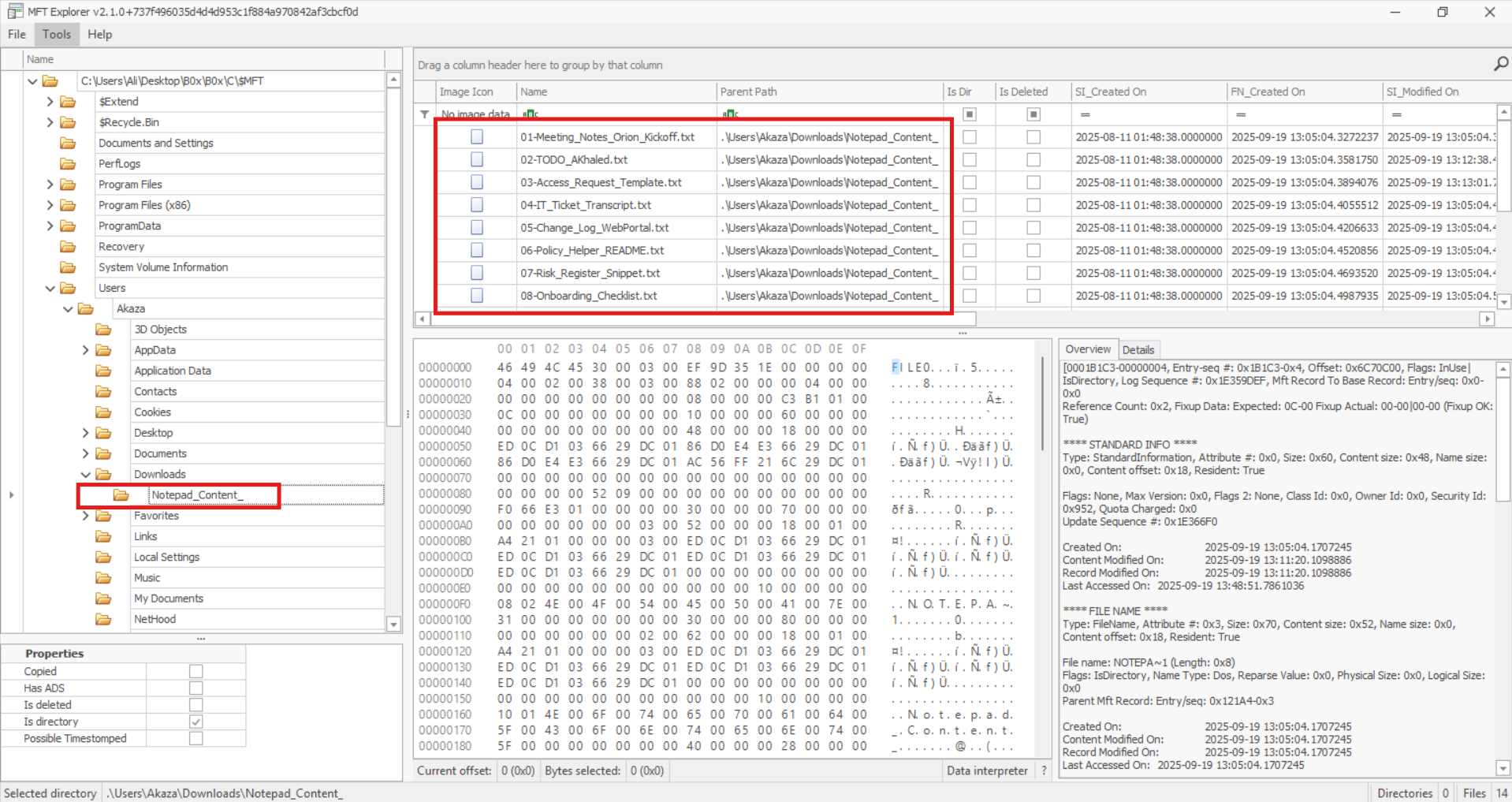
After checking through the contents, I eventually found the flag:
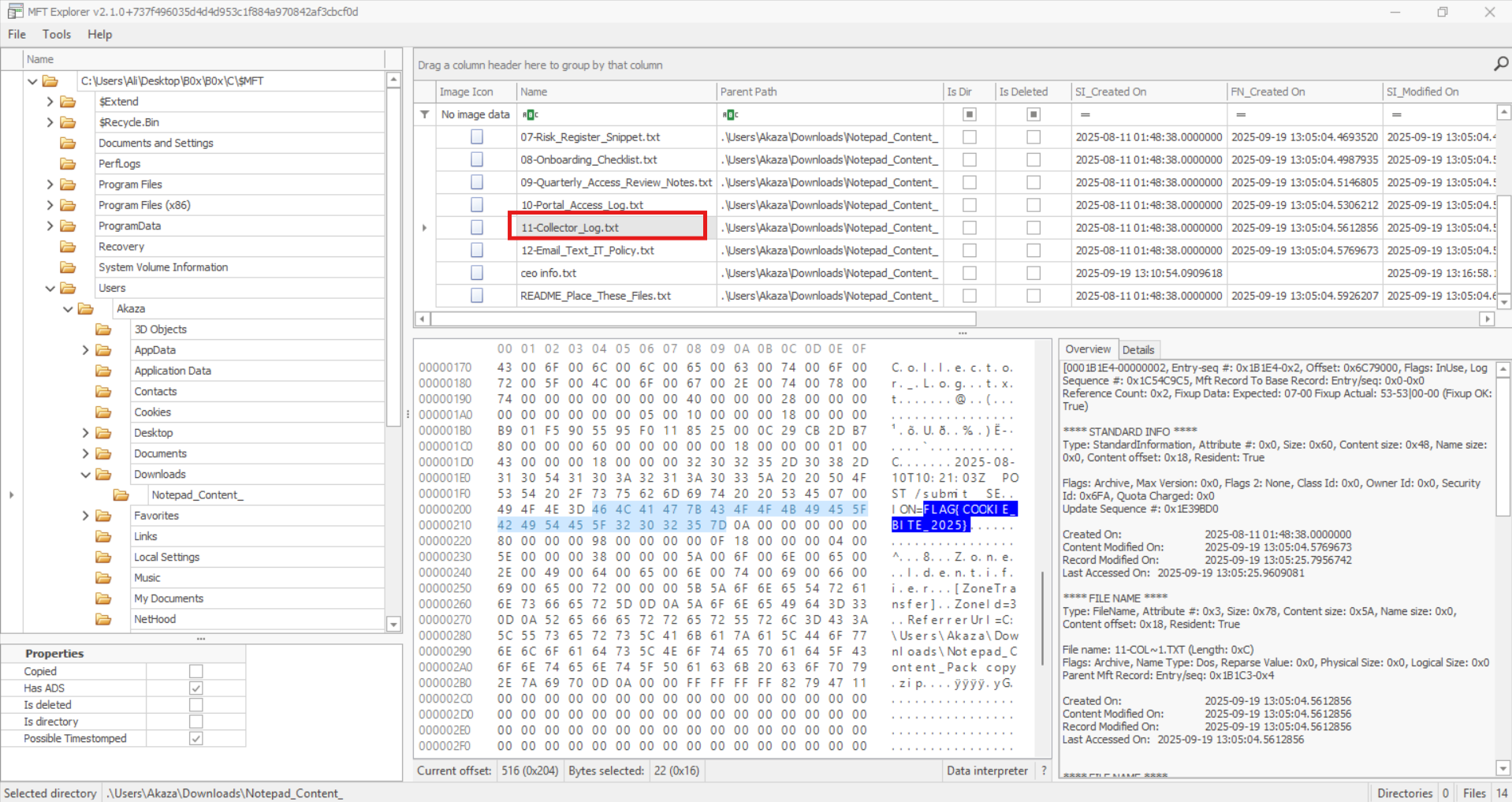
When I submitted it, the system rejected it because it didn’t match the competition’s required flag format. I then reviewed the ceo info file, which indicates something important about ceo and remembered that the challenge stated sensitive data had been stolen. Taking this into account, I noticed the hex value between the curly brackets in it, submitted it in the required format, and it was accepted:
Illusion

The challenge provided an .ad1 image that, when opened in FTK Imager, showed the following:

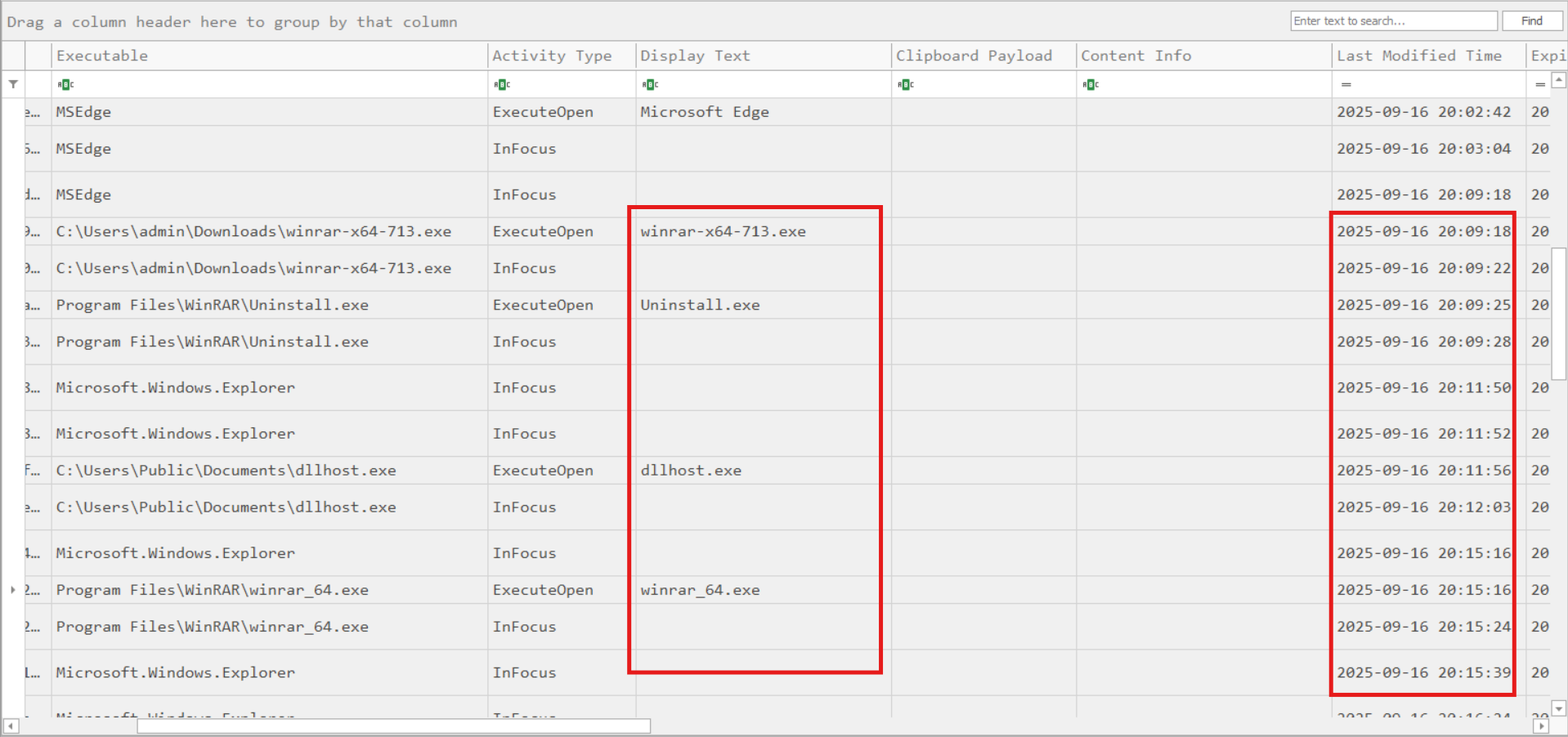
I started by examining ActivitiesCache.db and parsing prefetch files to get a high-level view of system activity:
Prefetch timeline:
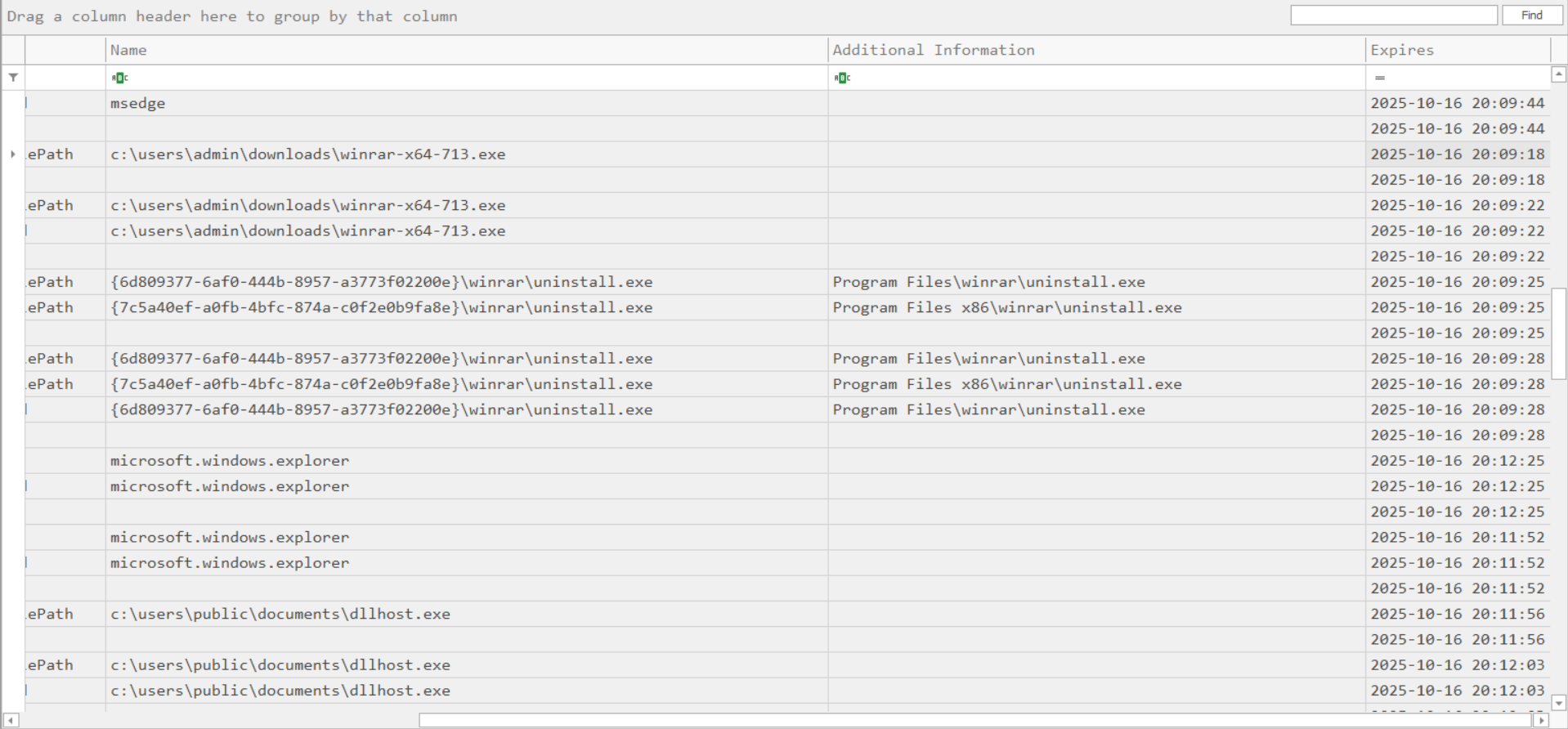
Next, I exported files to list them by last modification timestamp:

From this, I observed a WinRAR installation and an execution of dllhost.exe from the Public user’s Documents folder (an unusual location). I submitted the dllhost.exe file to VirusTotal and inspected its strings:
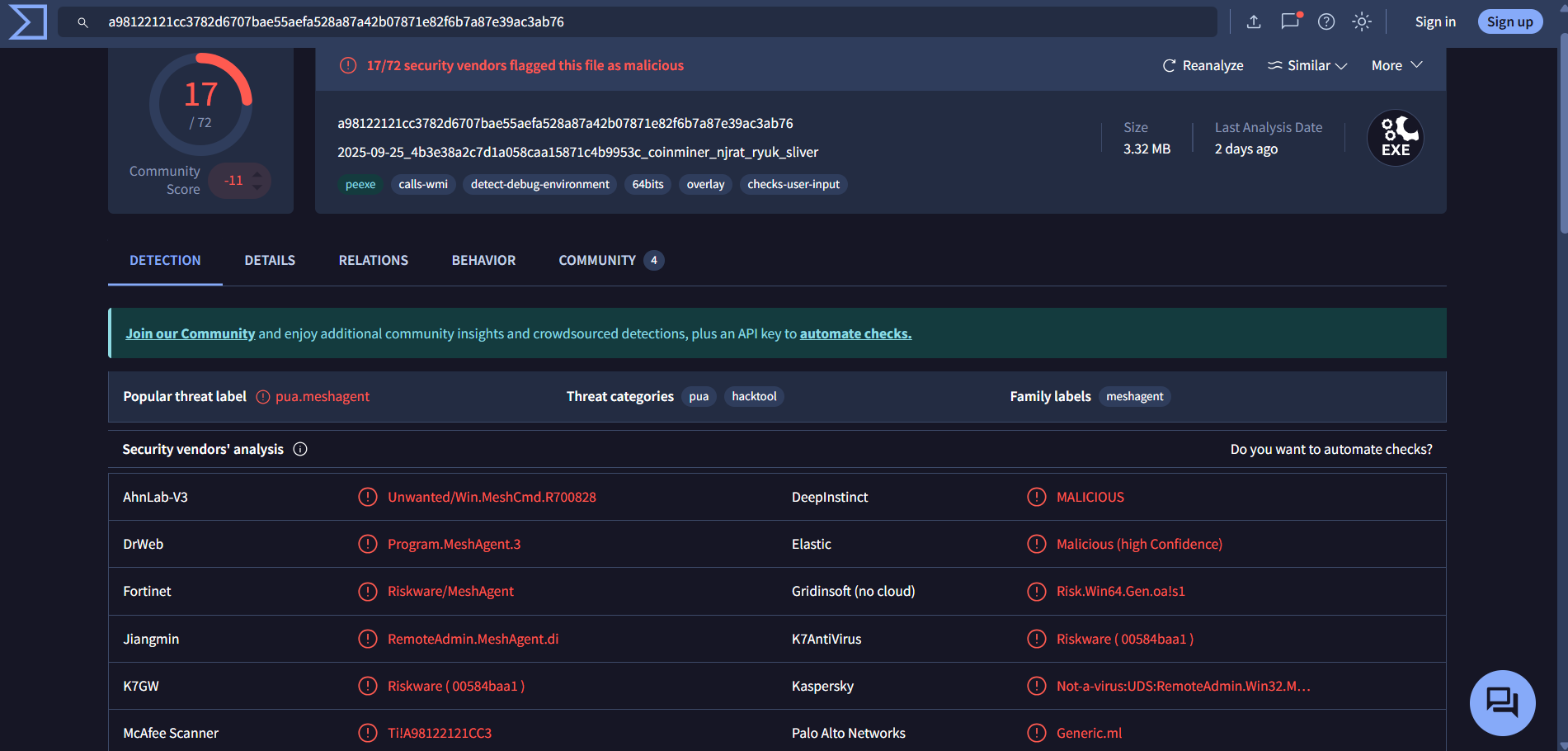
The binary appeared related to Mesh Agent (remote management), which suggested it might have been used when the challenge image was created rather than being part of the actual challenge activity. I paused work during the competition and continued later.
To understand what happened between the WinRAR installation and the dllhost.exe execution, I parsed the $MFT and focused on entries near that timeframe:
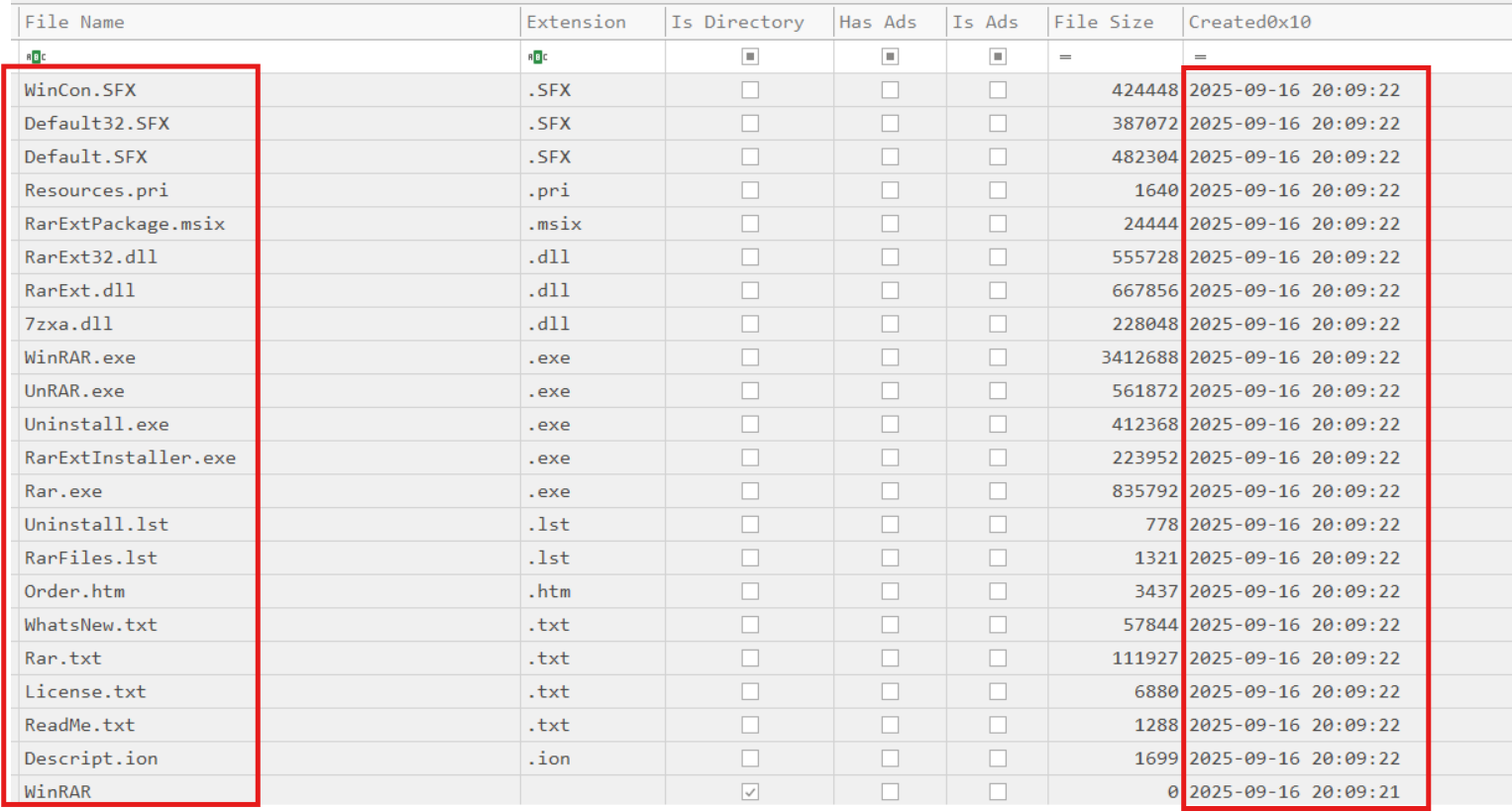
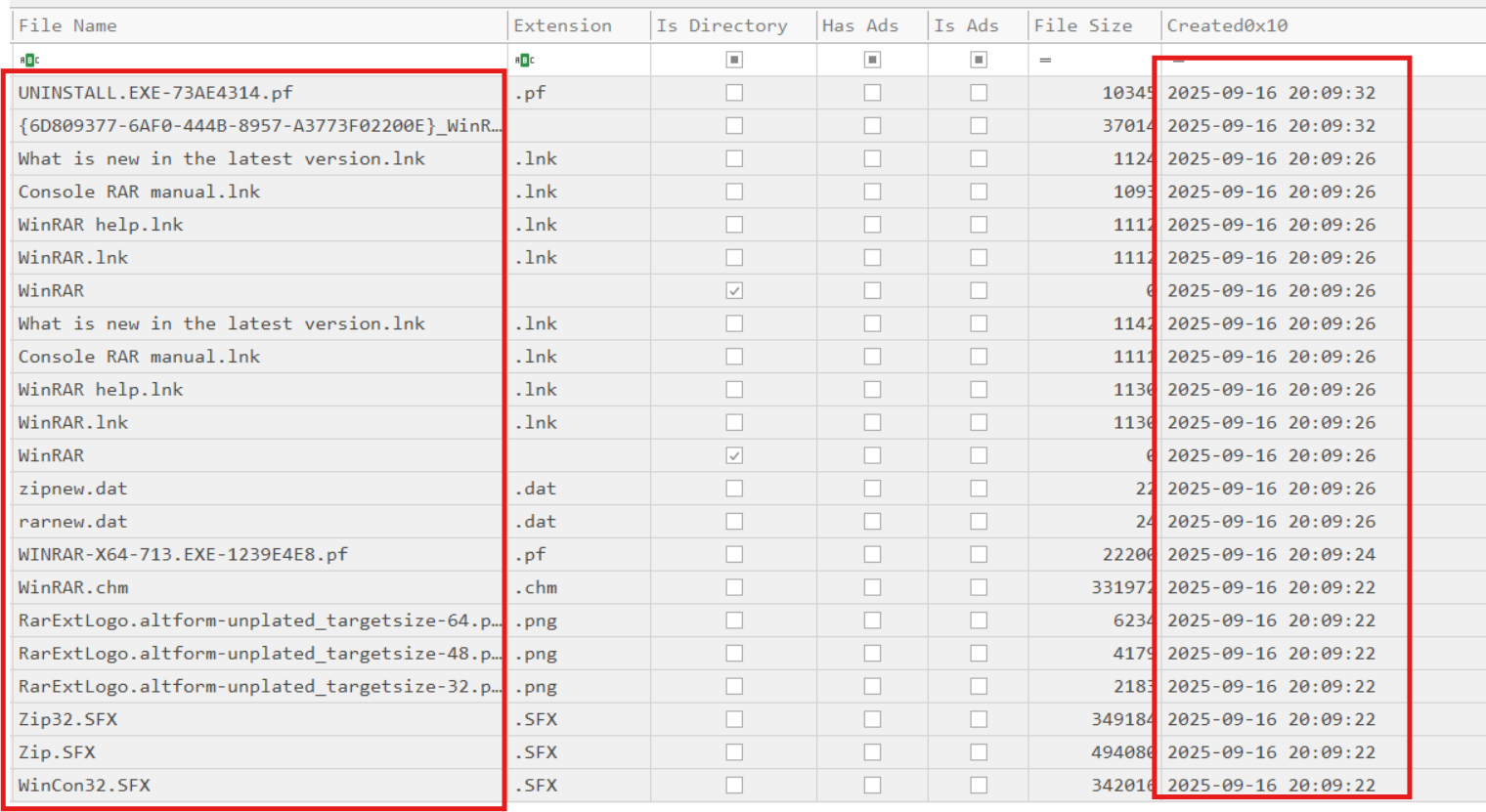
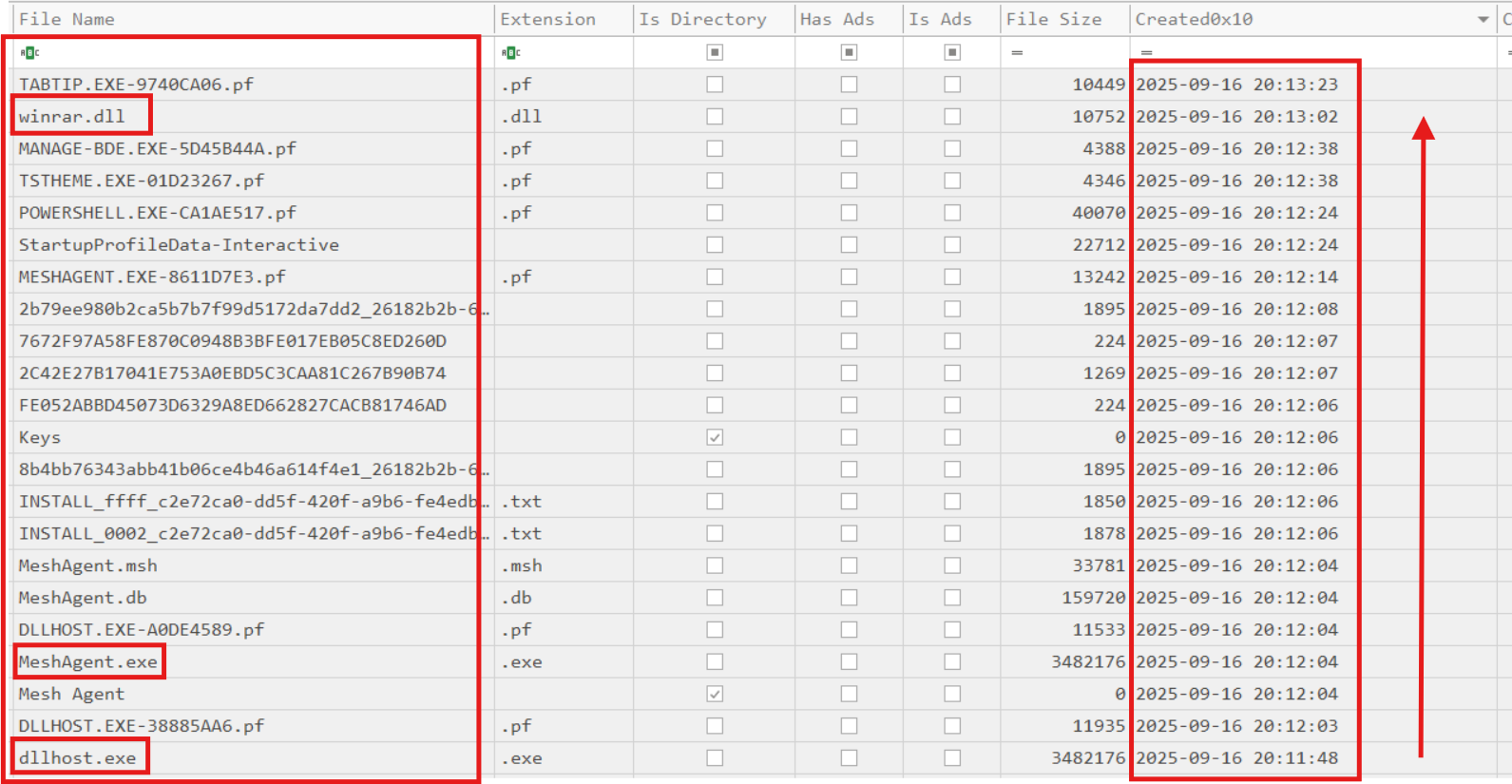
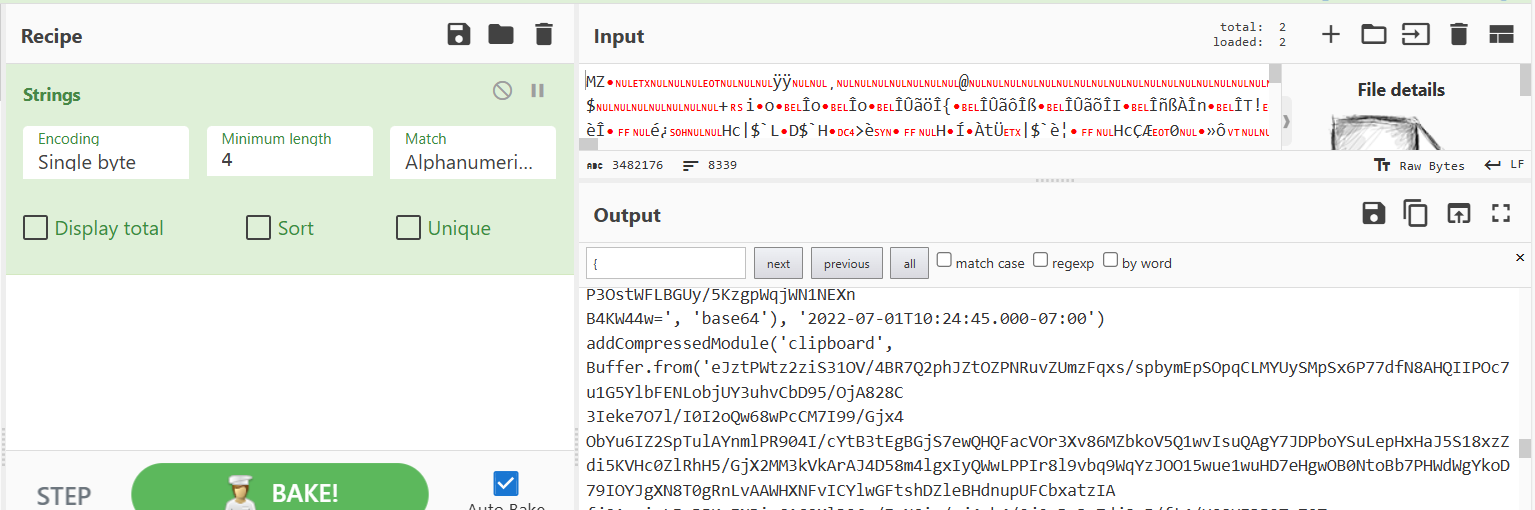
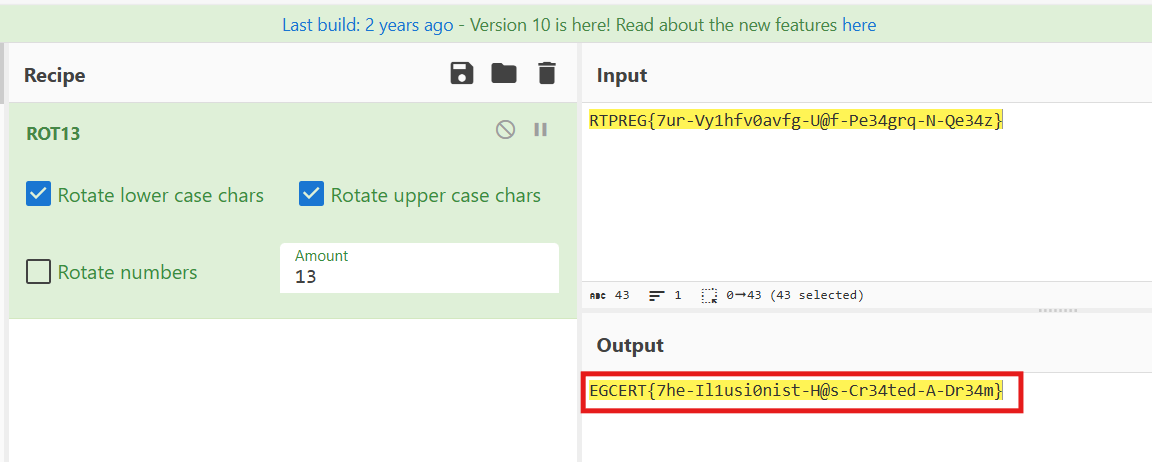
The timeline showed WinRAR installation completion, execution of dllhost.exe, then MeshAgent activity, and finally a write of winrar.dll into the WinRAR installation folder. I extracted winrar.dll, inspected its strings, found an encoded candidate, decoded it with ROT13 in CyberChef, and recovered the flag:

SilentByte
This challenge was straightforward. The image contained the following files:

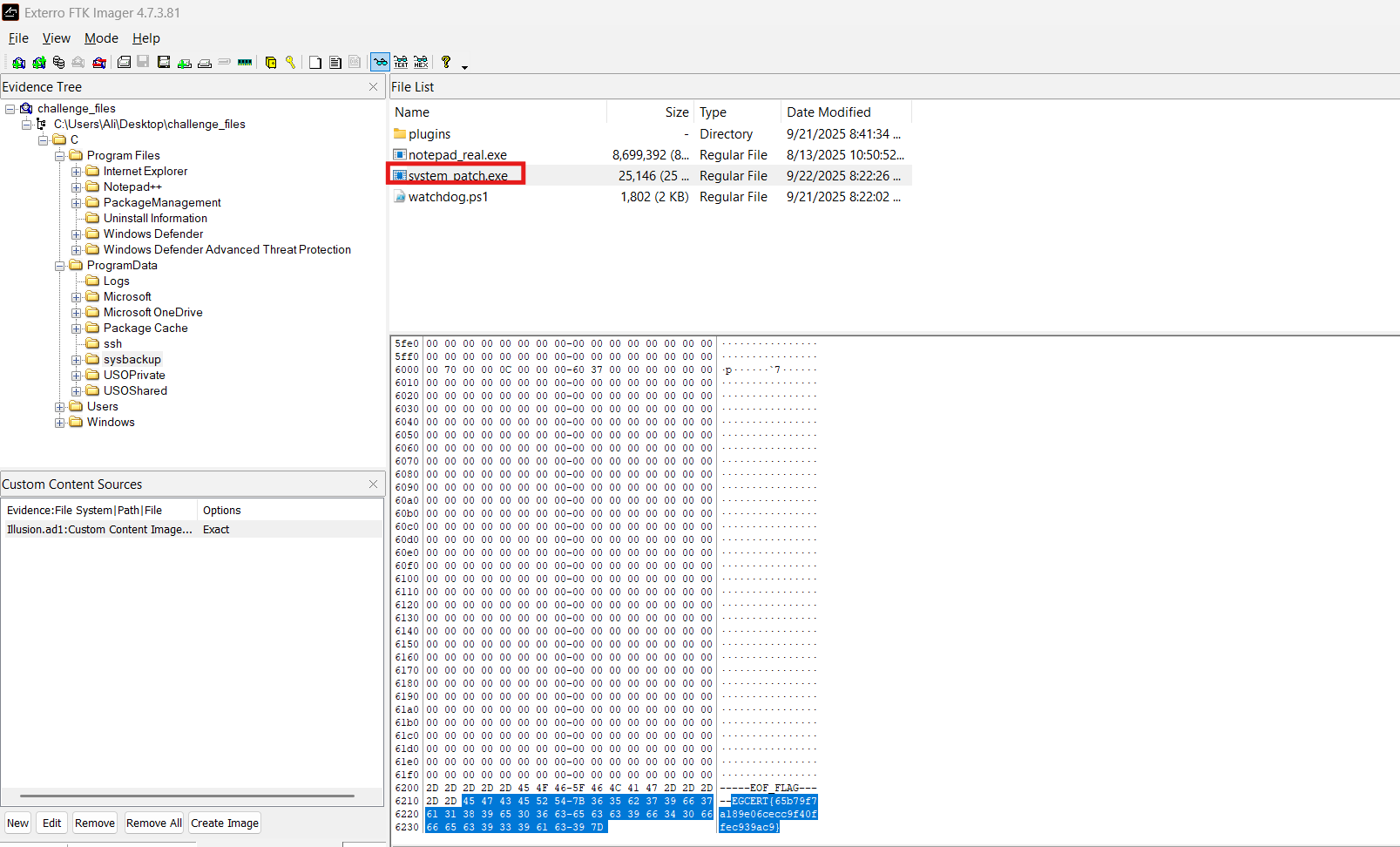
I opened the image in FTK Imager and navigated the file system. The challenge description mentioned patching applications; I confirmed Notepad++ was installed and discovered a sysbackup folder under ProgramData:
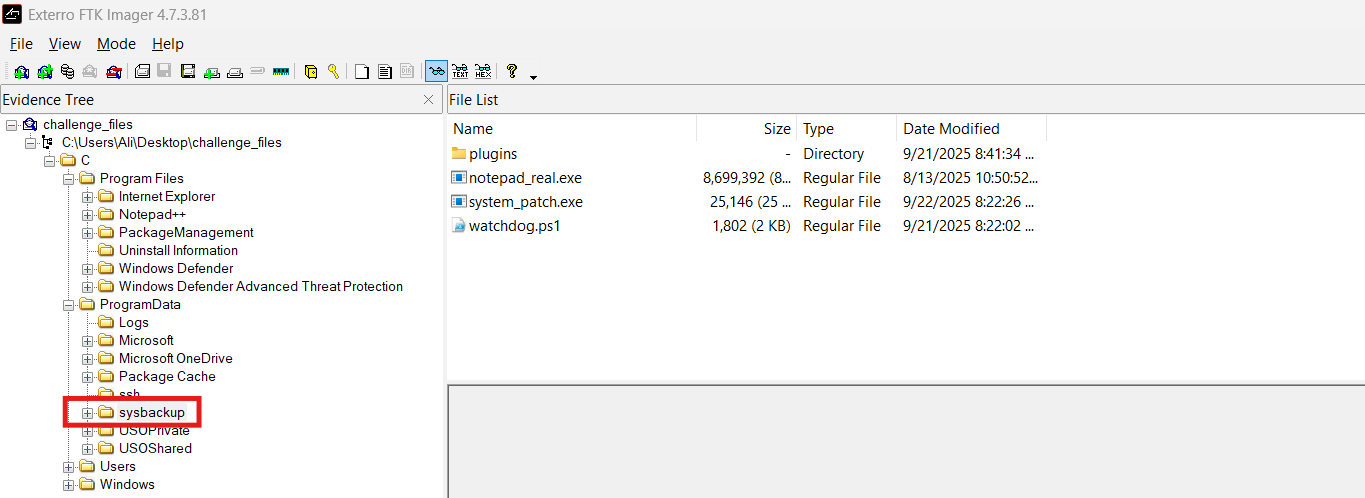
sysbackup contained several notable binaries. I inspected strings until I found the flag in plaintext inside system_patch.exe:
FindEvil
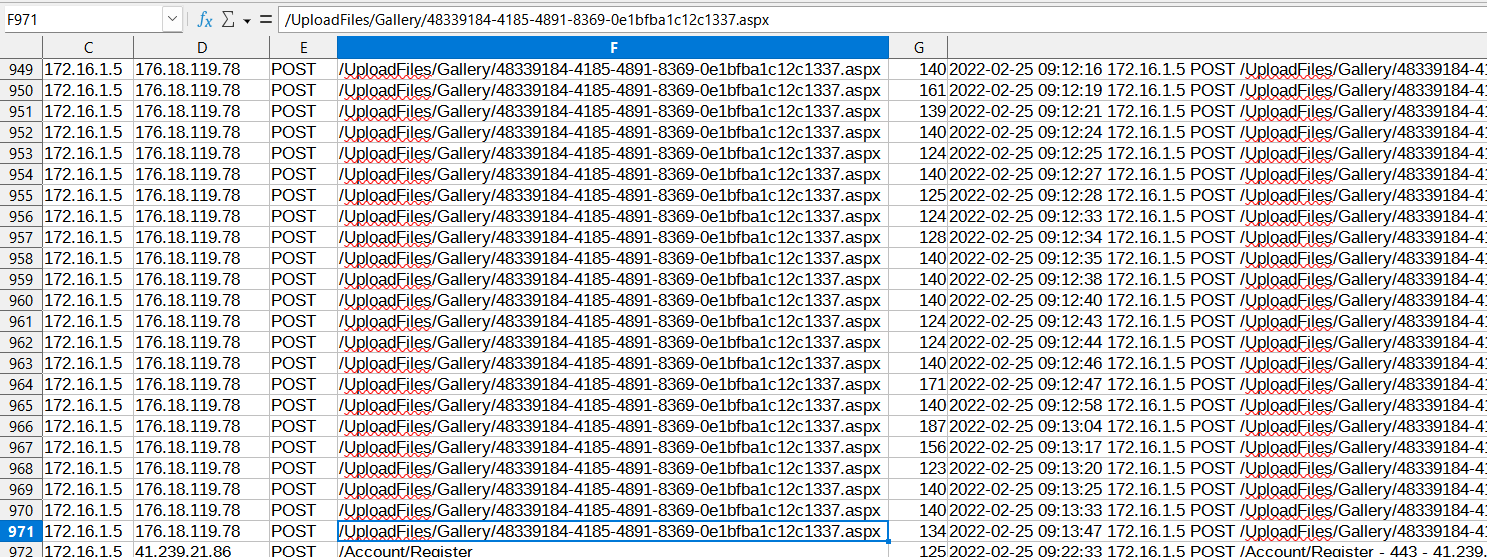
This challenge provided three web log files covering three consecutive days. I used ChatGPT to extract all POST requests from the logs and output them into a CSV for review. From that CSV I located the last web-shell and recovered the flag:
Those were all the forensics challenges from the final competition. I hope these writeups prove useful.
Thanks to my team, we secured 3rd place in the IEEE Victoris 4.0 CTF.