Introduction
SOAR (Security Orchestration, Automation, and Response) tools are designed to streamline and automate security operations, making it easier to respond to security incidents. Tines is a popular SOAR tool that offers a user-friendly interface and a wide range of integrations with various security tools. In this post, we’ll explore how to get started with Tines and set up a basic workflow
Practical Exapmle with IBM Qradar
- Retrieve all destination ips
- Check them with virustotal
- Send email (report) by the malicious ones
I’ve created a diagram of the required workflow:

1.0 Submit Search
Tines comes with large and great templates that we can use:
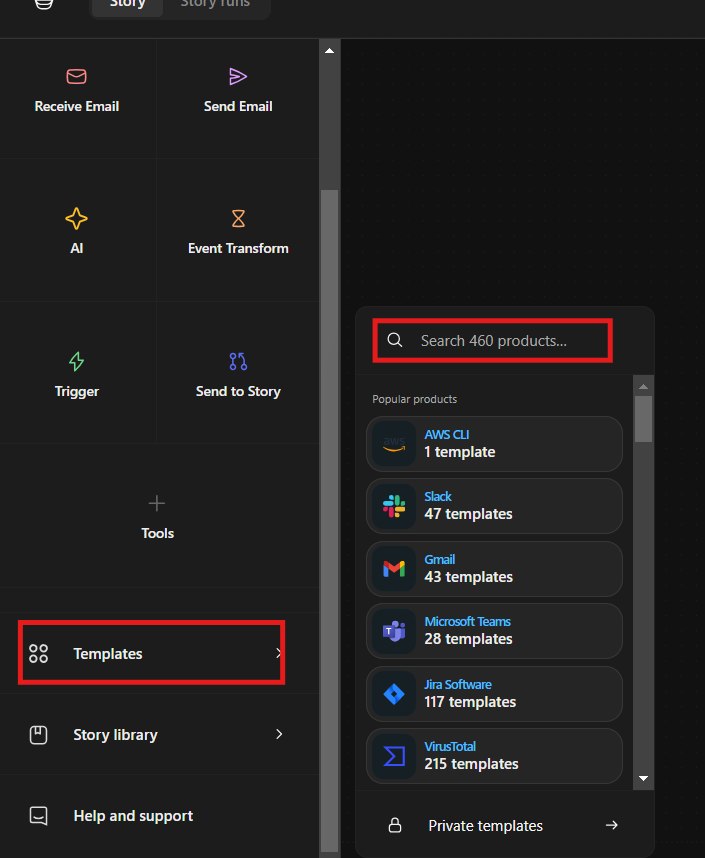 let’s search for “qradar”
let’s search for “qradar”
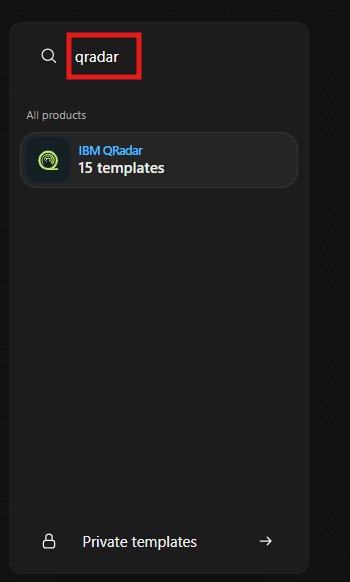
add the “Qradar” template to the workflow:
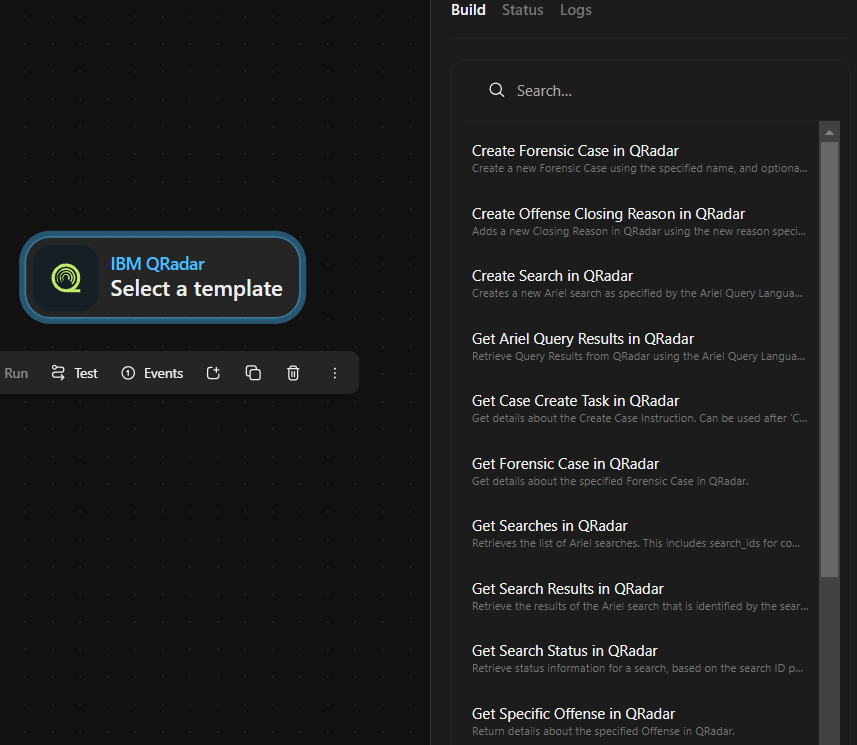
there are 15 templates available we can check one of them that we might need, we want to do search on IBM Qradar so we can search for “search”

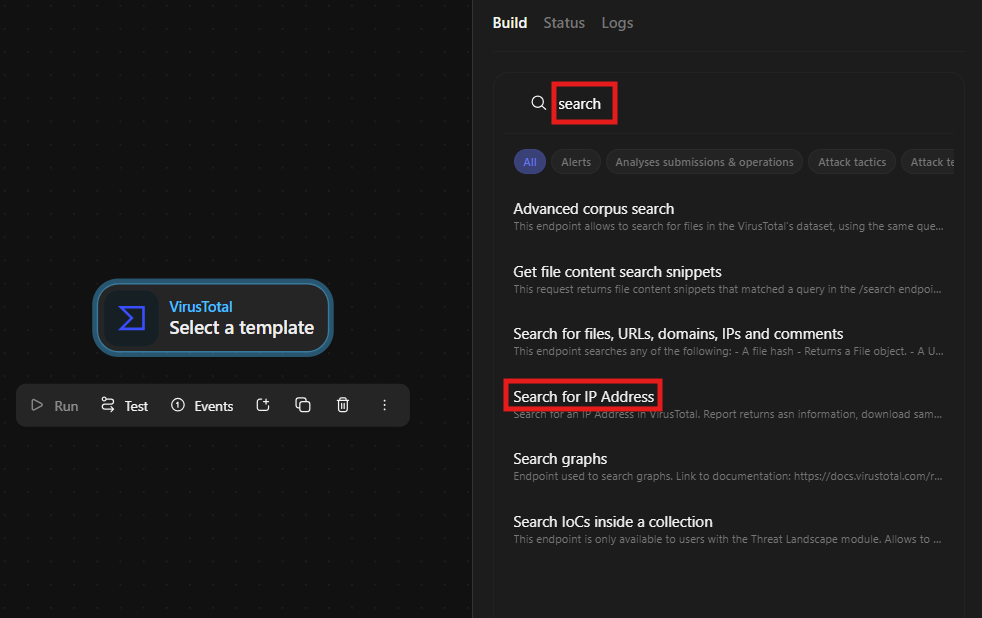
we have found a all related templates we will use “Submit Ariel Query in QRadar”, click on it
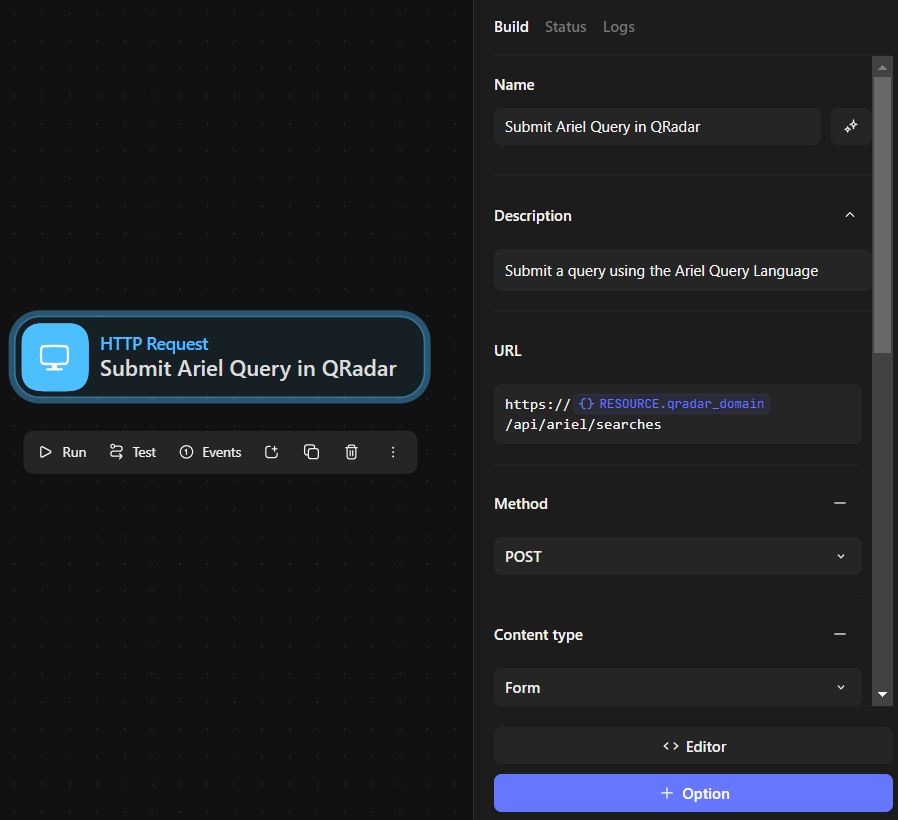
1.1 Configuring “Submit Ariel Query in QRadar”
we can use Editor so we can see the full Json script and edit from there or we can edit each field here:

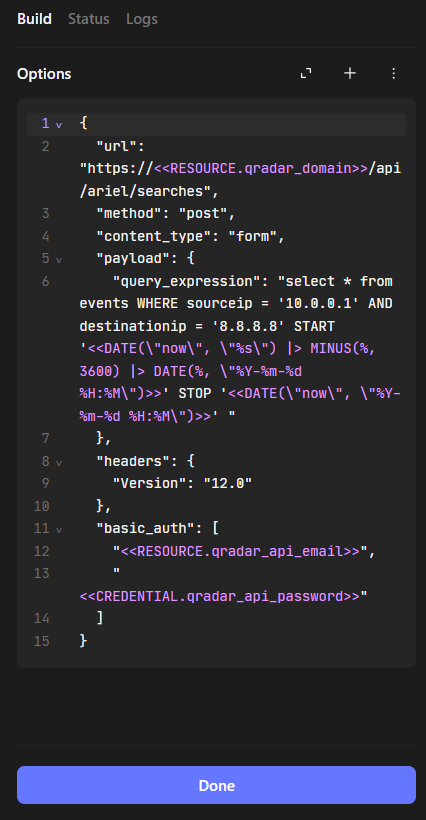 replace
replace <<RESOURCE.qradar_domain>> with the QRadar domain and edit query_expression I used this:
SELECT destinationIP FROM flows GROUP BY destinationIP limit 100 start '2024-09-01 12:00:00' stop '2024-09-08 12:00:00'
this query will return the destination ips from the last 7 days, you can change the query to suit your needs
under basic_auth enter your credential on your QRadar, my final script is:

Note
- Make sure to test the query in QRadar before running it in Tines
- I used
flowshere that related to Network activity in my accessed QRadar - I added
disable_ssl_verificationis related to my QRadar self-signed certificate.
Let’s test this: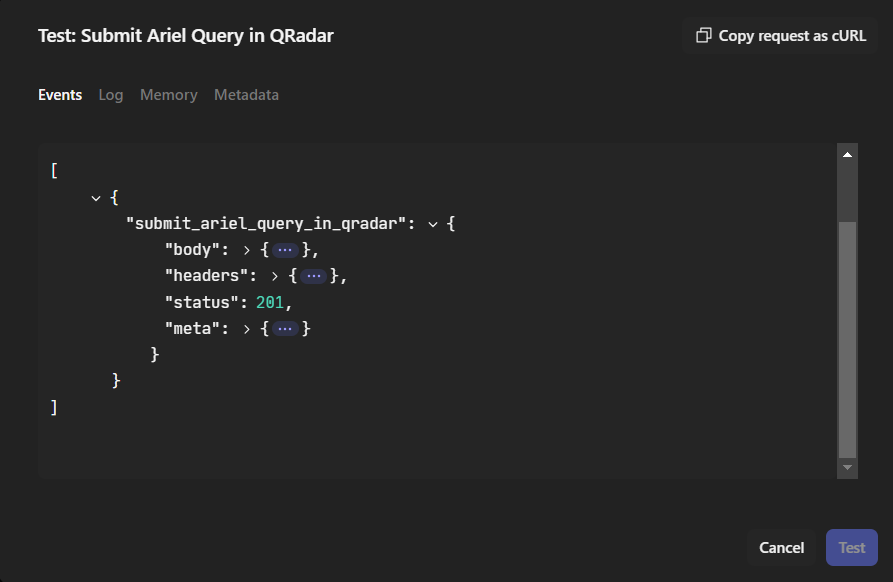
open body and scroll to findsearch_id
2.0 Retrieve Results
now we want to get the results:

2.1 Configuring “Get Ariel Query Results in QRadar”

configure URL by setting the cursor after searches/ till + button appear then click it and add value

Note
- Make sure runinng
Submit Ariel Query in QRadarone time at least then connect the two elements.
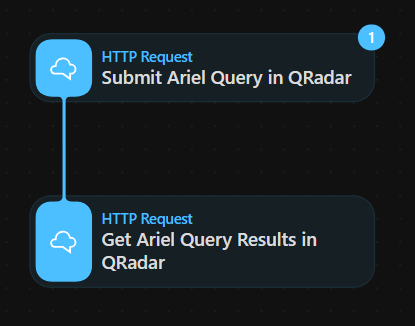
Once connected, Tines will suggest entries for you, choose and type [Enter] to continue

Tines suggests what data we can retrieve from it, choose Body

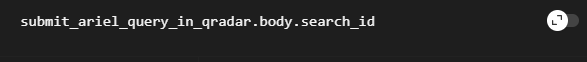
we can choose search_id to get search results

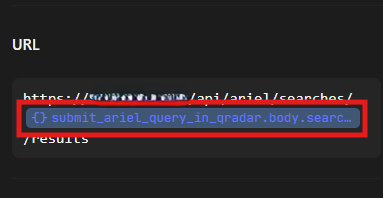
Note
- You can put
search_idyou got fromSubmit Ariel Query in QRadar.
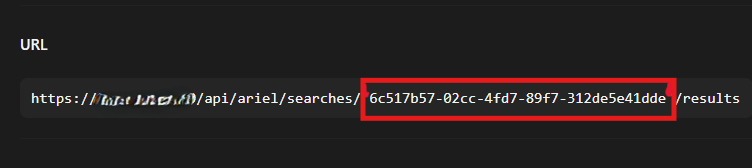
- For automating we created a formula to call
search_idfield from theSubmit Ariel Query in QRadarelement. Do not forget to fillBasic authwith your credentials
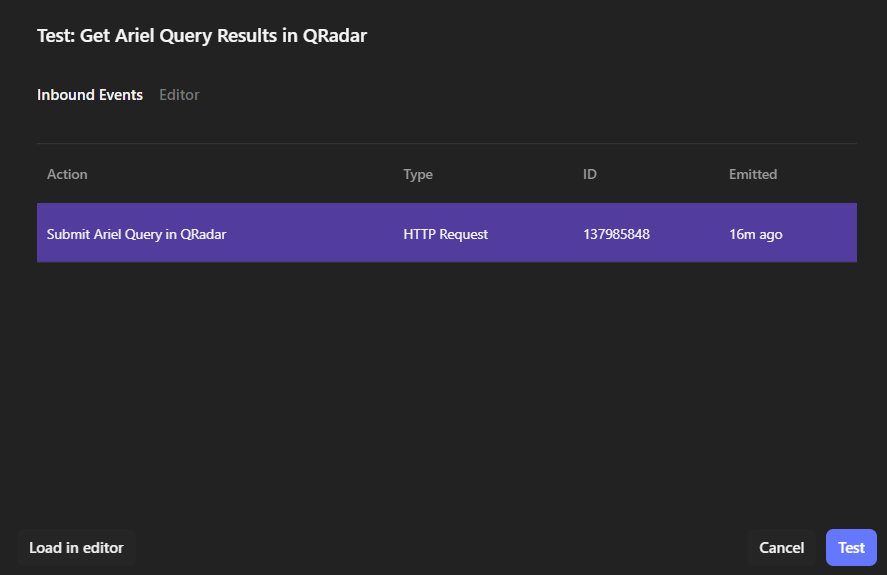
2.2 Testing
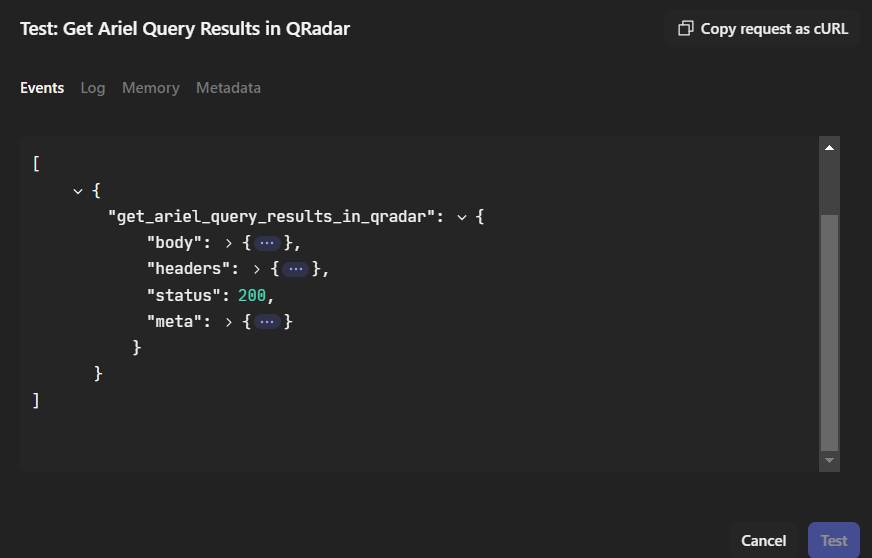
Now we can test:
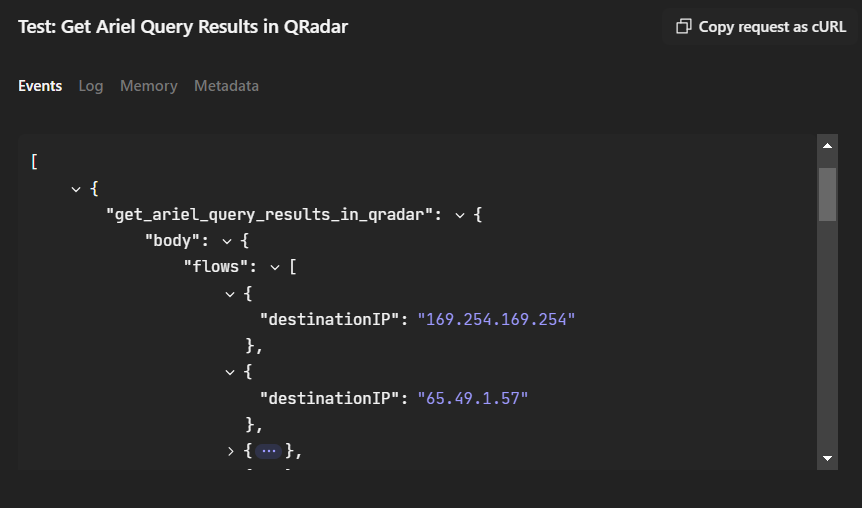
3.0 Extract Destination IPs
Now we got Destination IPs to extract valuse we use Event Transform

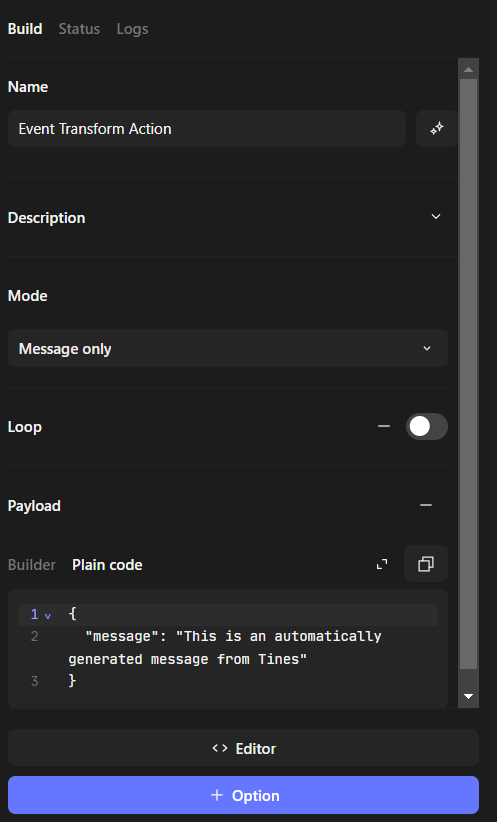
3.1 Configuring “Event Transform”
based on Tines docs event-transformation we use explode and set path to get_ariel_query_results_in_qradar.body.flows

3.2 Connect & Run

Check Event Transform Events


4.0 Search For IPs
Now we have Destination IPs, To search for them in Virus Total we check virustotal templates
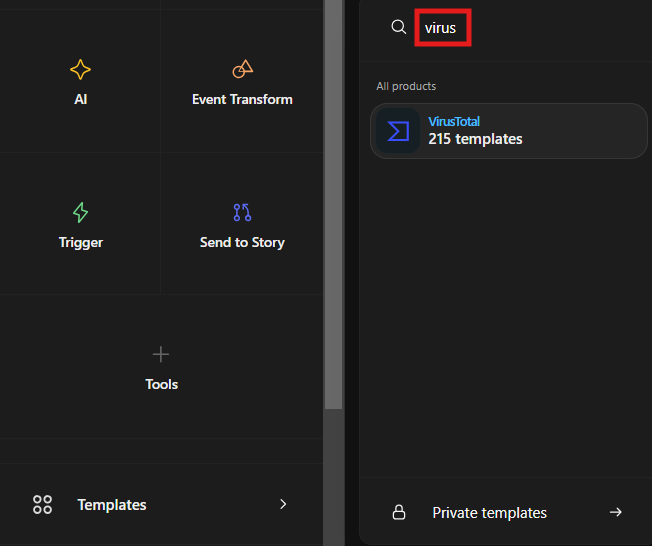
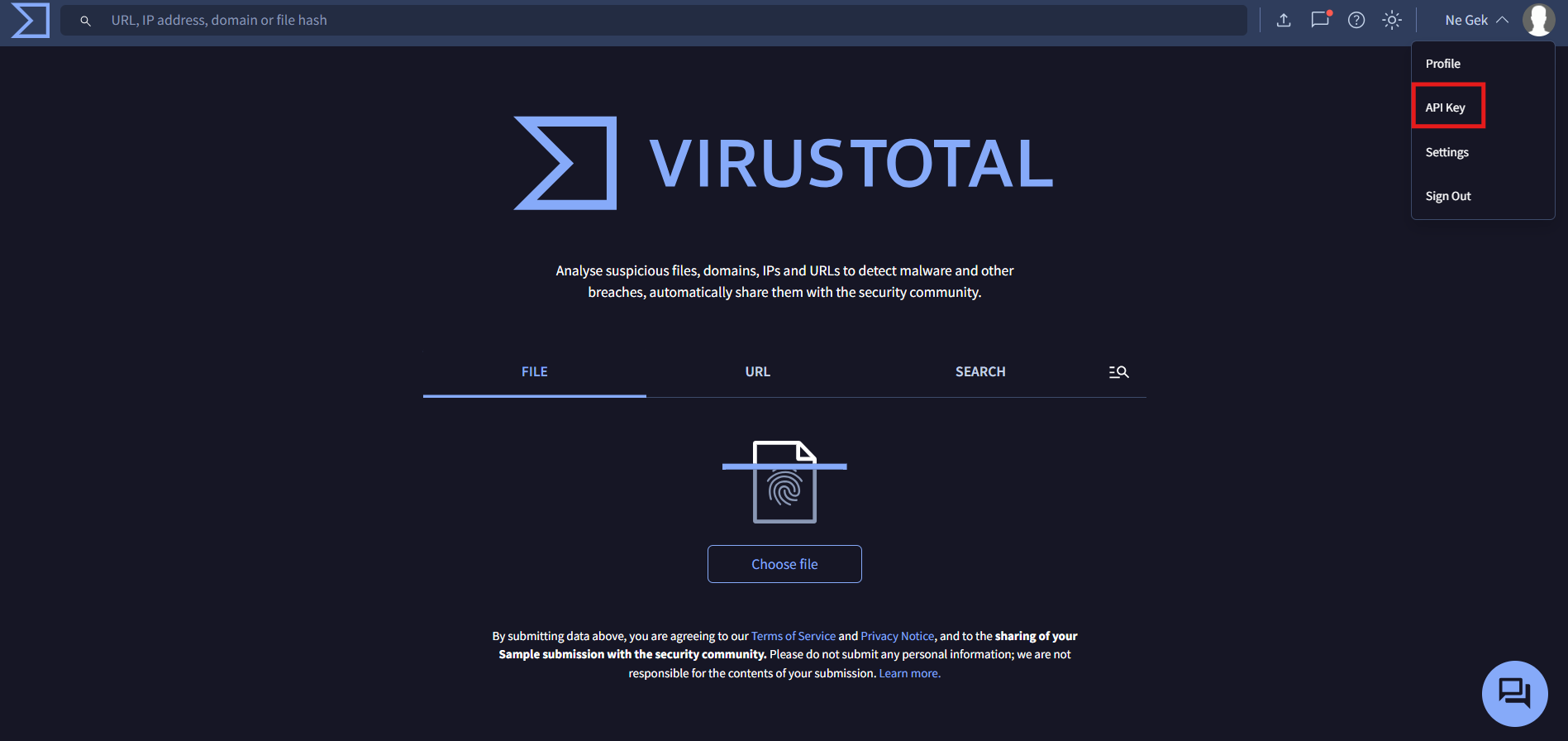
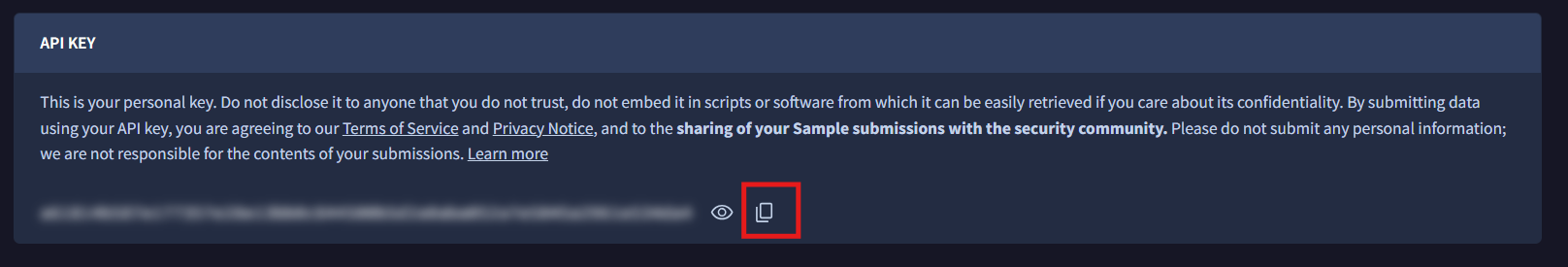
Create an account on VirusTotal and get your API key:
4.1 Configuring “VirusTotal - Search for IP Address”
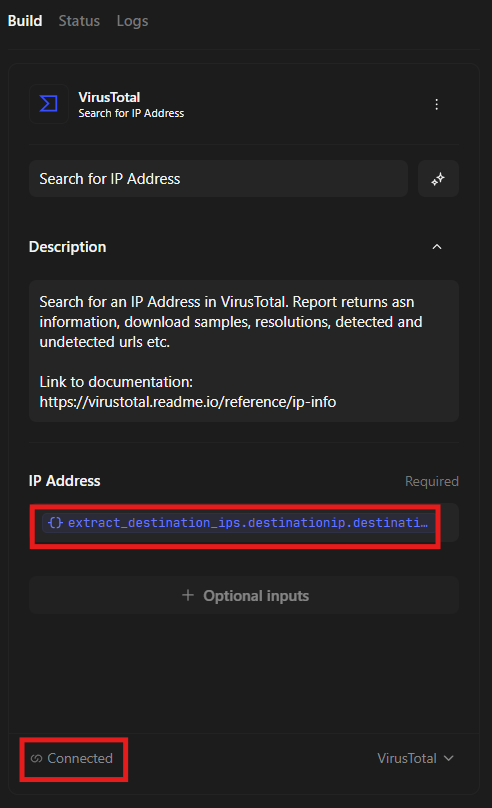
you will have connect button just click it and follow the easy setup
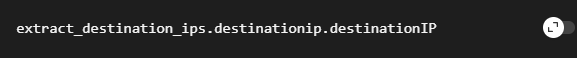
set IP Address to
Connect and run

check Events

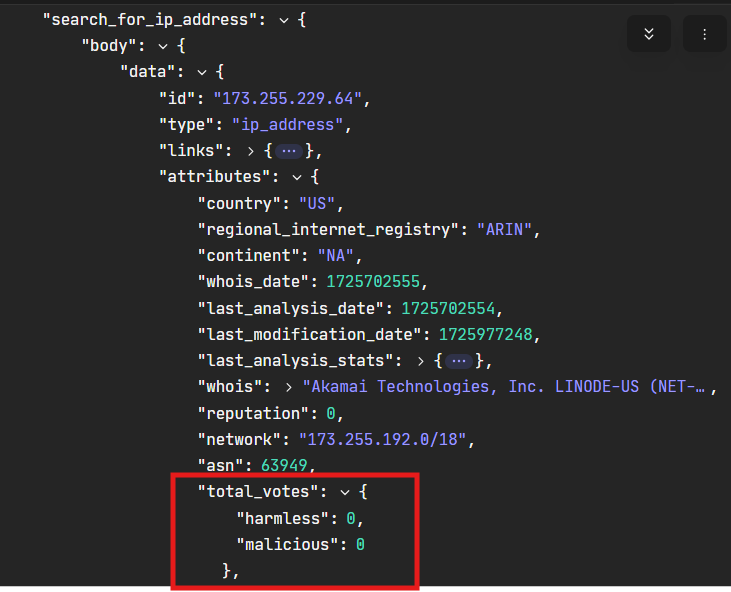
5.0 Is IP Malicious?
Now we have results from Virus Total, we can check if IP is malicious or not. We use Trigger to put a condition

5.1 Configuring “Trigger”
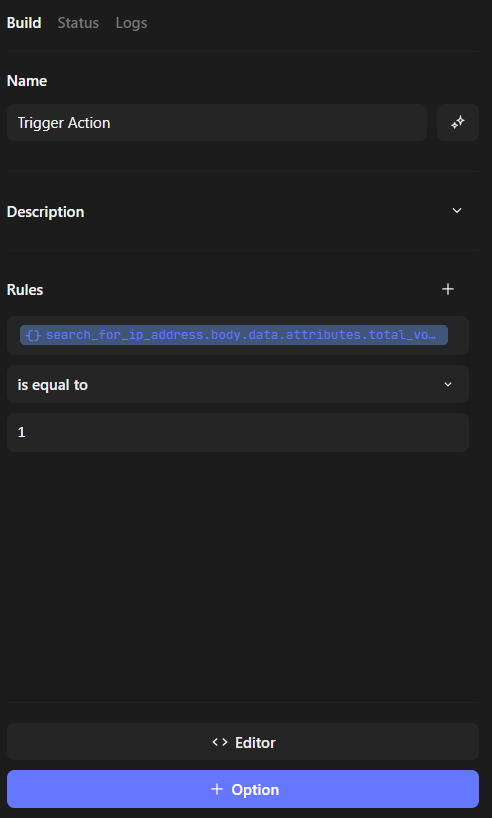
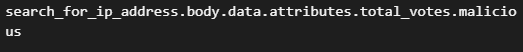
We checked that if the malicious equals 1 from total_votes retrieved from VirusTotal we will trigger the action
6.0 Alerting
Now we have a condition to trigger an action, we can use send email to send an alert email

6.1 Configuring “send email”
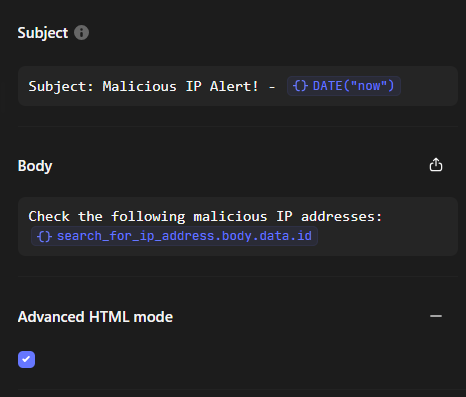
I added time to subject by DATE("now") formula and malicious IP by search_for_ip_address.body.data.id
7.0 Final Run

7.1 Checking emails

Conclusion
In this post, we have demonstrated how to integrate QRadar with VirusTotal using Tines. We have created a workflow that submits an Ariel query to QRadar, retrieves the results, extracts the Destination IPs, and then uses VirusTotal to check if the IP is malicious. If it is, we trigger an action to send an email to the security team.
This is a basic example and can be extended to include more features, such as checking multiple IPs or including additional information in the email.
References
[1] Tines Documentation: https://docs.tines.io/
[2] Tines Blog: https://blog.tines.io/
